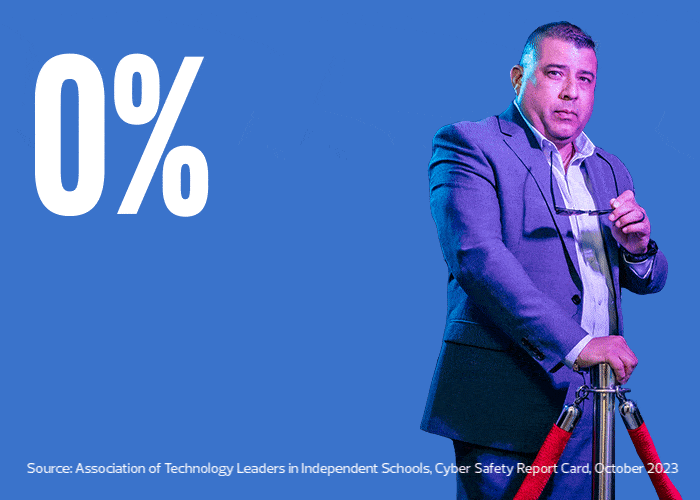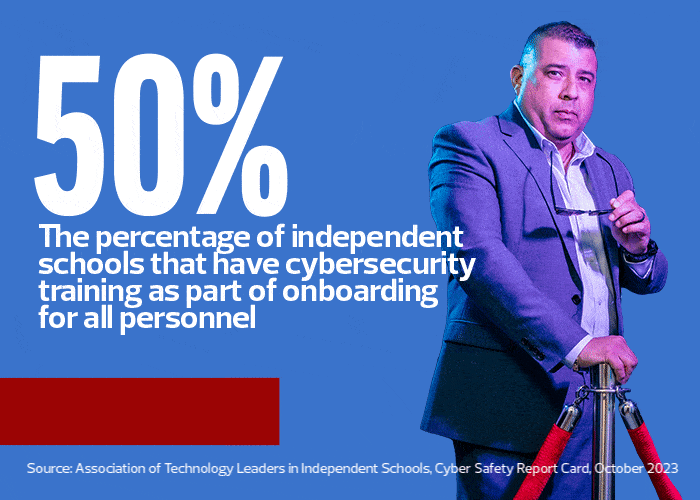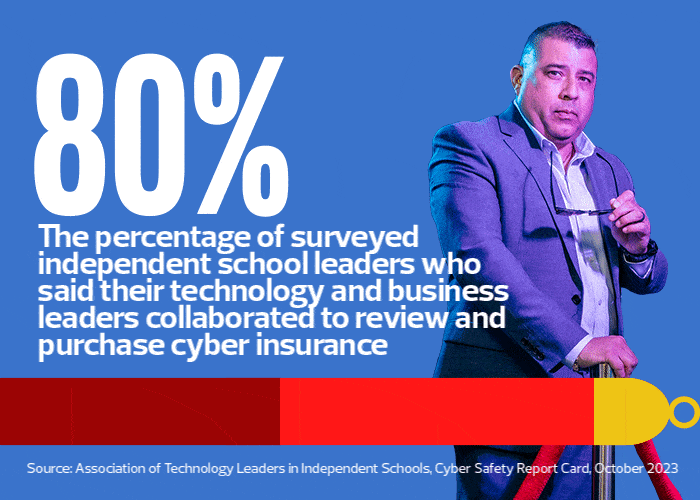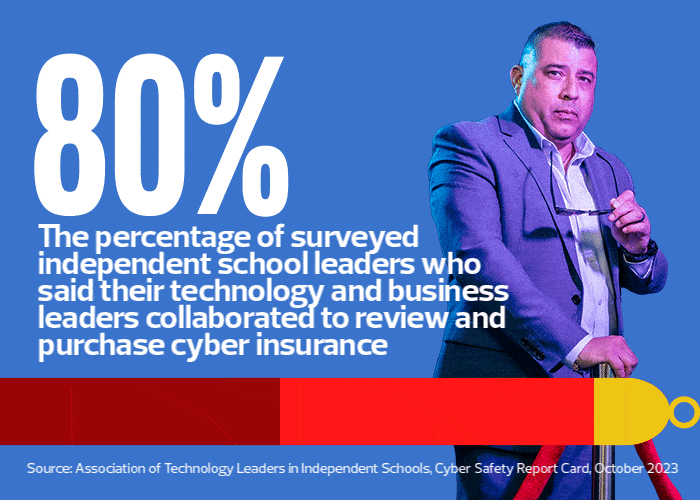
Among K–12 institutions, private and independent schools are particularly attractive targets because they charge tuition, offer financial aid and fundraise. So, they store an even greater amount of financial and sensitive information — a potential goldmine for hackers. As a result, Valerio says, rapid responses to cybersecurity incidents are critical.
For example, if a student clicks on a questionable website and downloads malicious code, security software notifies Valerio immediately. He calls the teacher in the classroom, who tells the student to bring the laptop to the IT department within five minutes for inspection and remediation.
“No one is immune to attacks, so you have to be proactive,” says Valerio, who is also the Florida school’s CTO and a Microsoft MVP. “I’ve put all these security barriers in place so when something triggers an alert, we are on it immediately. It doesn’t matter the time of day or day of the week. We are on it 24/7/365.”
RELATED: How to choose and integrate new technology vendors.
Private and Independent Schools’ Cybersecurity Needs
To prevent data breaches, private and independent school IT leaders safeguard their IT infrastructure and computing devices just like their public-school counterparts: by taking a comprehensive approach to security through a mix of technology, policies and people. But, as with all schools, some do it better than others depending on their budget and tech expertise.