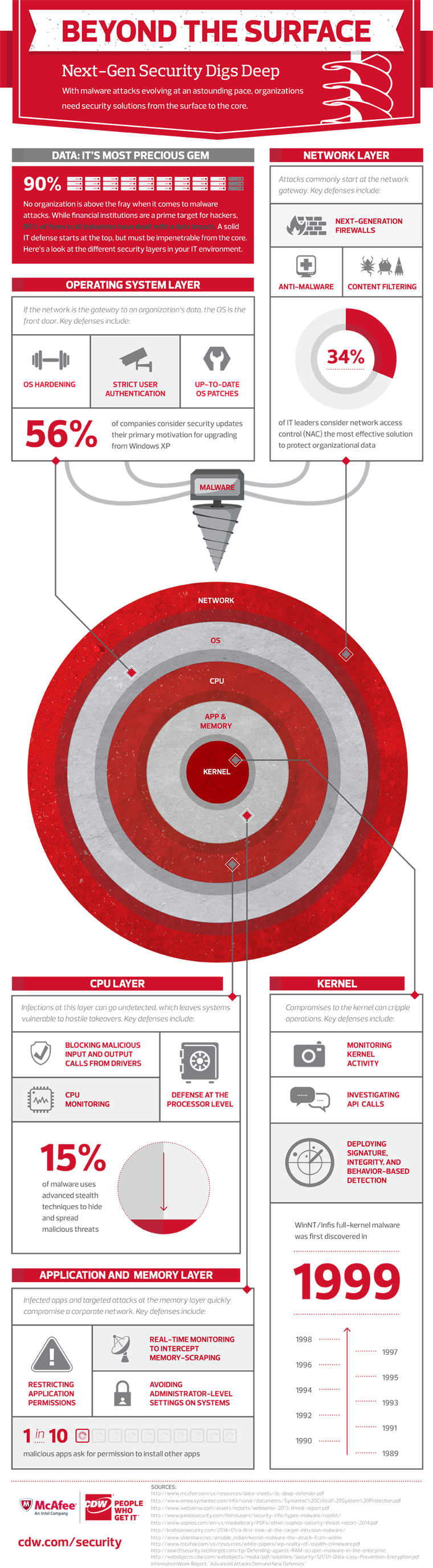
How Many Layers Does Your Security Solution Protect? [#Infographic]
The Target data breach, which rocked the retail world, was remarkable on several fronts, but perhaps chief among them was the fact that the critical data snagged by the malware baddies wasn’t in a hard drive. It was scraped straight from the memory, according to a report from InformationWeek.
Examples like the Target incident make it critical for organizations to examine their IT security from multiple layers. Think about protecting the network, the operating system, the memory and yes, even the processor of your computing devices.
CDW•G has gathered research and survey information and compiled it into an infographic highlighting the layers of true next-generation security solution. Similarly to how the layers of the earth envelope the earth’s core, a modern IT security solution must protect its IT environment to the core.
With an estimated 15 percent of malware using advanced stealth techniques, adding protection to the enterprise IT environment on all fronts is no longer an option, but a necessity.
Check out the full infographic from CDW•G below.