Now more than ever, universities need to maintain the highest levels of IT security. According to a recent report by Opinion Matters and VMware, 70 percent of respondents said that cyberattack volumes at their organizations have increased in the past 12 months. This includes 73 percent of respondents who said their departments suffered security breaches within the same period.
These challenges underscore the need for universities to strengthen their security operations centers. VMware Carbon Black Enterprise EDR provides advanced threat hunting and incident response capabilities for vital visibility to universities’ top IT security personnel.
A Centralized Viewpoint: Consolidate Cloud Security
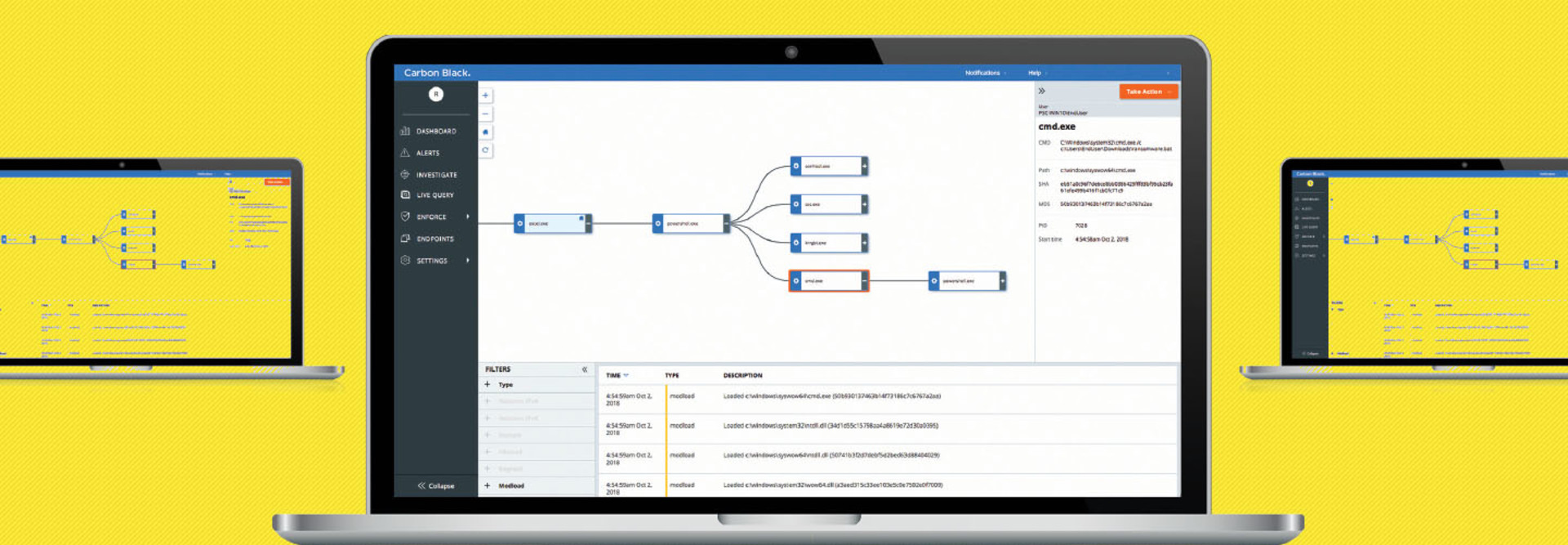
This surprisingly easy-to-use enterprise endpoint detection and response solution is part of the larger VMware Carbon Black Cloud platform and offers state-of-the-art capabilities. These include a robust partner ecosystem and an open platform that lets university security teams integrate Enterprise EDR into their existing security stack via automation and open application programming interfaces.
Enterprise EDR provides IT teams with next-generation endpoint detection and response that consolidates security in the cloud and aggregates all data into a simple console and data set that provides real-time network analysis. By collecting data continuously and leveraging the VMware Carbon Black Cloud, Enterprise EDR provides the most comprehensive view of an attack and produces results in minutes.
LEARN MORE: Get the Defense-in-Depth strategy checklist.
Complete — Yet Simple — Endpoint Data Aggregation
Enterprise security teams often struggle with finding the endpoint data necessary for proactively investigating abnormal behavior. Security and IT professionals often lack the ability to see beyond suspicious activity and must dive deeper into the data to extrapolate actionable intelligence.
I found that Enterprise EDR eliminates most issues that plague more complicated platforms by providing end-to-end visibility. This starts with an easy deployment that includes automated updates and continuous endpoint visibility. In minutes, I could launch and accelerate investigations into testbed anomalies and discover the root cause of simulated attacks.
Using threat hunting in conjunction with powerful programs such as Enterprise EDR, university IT teams can prevent extensive damage to sensitive data and reduce interruptions to critical campus operations.
SPECIFICATIONS
HOSTED SERVICE TYPE: Cloud-native endpoint protection
RETAIL/LICENSING: License
OPERATING SYSTEMS: Out-of-the-box and customizable behavioral detection
SETUP: Out-of-the-box and customizable behavioral detection
REMEDIATION: Secure Shell for rapid remote connections
INTELLIGENCE FEEDS: Proprietary and third-party threat intel