Why Higher Education Is the Target of Hackers, Phishers and Spammers
Data security is an important topic in higher education today. Colleges have sensitive data to protect, and more vulnerabilities are popping up every day. Symantec’s 2013 Internet Security Report goes into great detail about the evolving risks to data and the best practices for safeguarding it. We recommend downloading and reading the entire report, but here we offer a few key takeaways that are particularly applicable to the higher education community.
The Education Sector Is at Risk

While the healthcare industry is the favorite target of hackers and malware, education beat out government for second place.
What exactly does this mean for the higher education community? Considering the treasure troves of personal and financial data that universities store, it’s hardly surprising that they’re targets. As stewards of public data, there is pressure on colleges to invest in highly secure systems:
Healthcare, education, and government accounted for nearly two-thirds of all identities breached in 2012. This suggests that the public sector should further increase efforts to protect personal information, particularly considering how these organizations are often looked upon as the custodians of information for the most vulnerable in society.
It should be noted that many public organizations, including governments and schools, are required to report data breaches; private businesses are typically not required to do so. While this can skew the data, it does not lessen colleges’ burden to keep their student and faculty data safe.
Data Is Hacked, Not Lost
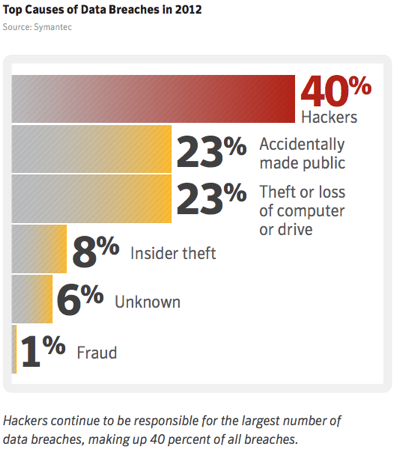
In 2012, a full 40 percent of data breaches came at the hands of hackers. Mobile trends like BYOD (bring your own device) and cloud computing put more data in the hands of users, creating considerable concern about the safety of that data. For this reason, mobile device management software has made its way onto many smartphones and tablets over the last several years. As it turns out, lost or stolen devices don’t pose anywhere near the threat that hackers do. With that in mind, universities cannot afford to be lax with their BYOD programs and cloud offerings. As a best practice, it’s often wiser to hand off services like the cloud to a trusted vendor rather than try to build a system in-house.
In order to successfully defend against hacker attacks, colleges need to develop and maintain a well-rounded security infrastructure, ensuring that all endpoints are protected, to prevent infiltration into data centers, networks and databases. This is an intimidating task, but one that colleges will have to deal with in the foreseeable future.
Mobile Is Vulnerable
Mobile devices have become susceptible to data breaches and malware for a number of reasons. First, the astonishing growth of smartphones and tablets is outpacing the infrastructure needed to secure the devices. Second, app stores offer portals for users to download applications and opportunities for hackers to plant malware directly onto hard drives. And finally, social media sites are a huge target for hackers and accidental data loss and are used heavily on mobile devices. Symantec explains how social media is leading to data weaknesses:
Social media combines two behaviors that are useful for criminals: social proof and sharing. Social proofing is the psychological mechanism that convinces people to do things because their friends are doing it. For example, if you get a message on your Facebook wall from a trusted friend, you’re more likely to click on it.
Sharing is what people do with social networks: they share personal information such as their birthday, home address, and other contact details. This type of information is very useful for identity thieves. For example, your social media profile might contain clues to security questions a hacker would need to reset your password and take control of your account.
Moreover, many mobile applications frequently rely on cloud-based storage, and without an Internet connection are often limited in their functionality. Many more people and businesses are routinely using cloud-based systems, sometimes without even realizing it.
The bank robber Willie Sutton famously explained why he robbed banks: “Because that’s where the money is.” Online criminals target social media because that’s where the victims are.
The Good News? Email Spam Is Down
It’s not all doom and gloom for higher education security professionals. Email spam dropped 29 percent in 2012, although this is largely due to the migration of hackers and spammers to social media:
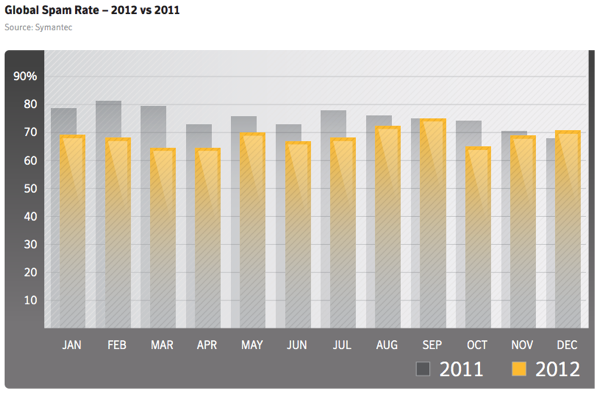
Spam rates declined for a second year in a row, dropping from 75 percent in 2011 to 69 percent of all email in 2012. In 2011 we were reluctant to call this decrease in spam a permanent trend. Botnets can be rebuilt, new ones created. But several factors appear to be keeping spam rates lower than in previous years.
This is not to say that the problem of spam has been solved. At 69 percent of all email, it still represents a significant amount of unwanted messages.
Security is evolving, and IT is often tasked with not just keeping technology running smoothly but also protecting the most sensitive data a university has.
How can colleges keep up with the ever-changing security landscape? Let us know your thoughts in the Comments section.








