5 Tips for Securing Windows Desktops
Whether physical or virtual, desktop security isn't just about making sure antivirus software is up to date. Hackers compromise valuable data via the weakest link — users — so ensuring desktops are appropriately secured is vital. These five tips can help ensure that your organization doesn't become an easy target.
Start Using Standard User Accounts
The Principle of Least Privilege is the concept of operating a computer with the minimum level of access required to complete a given task. In desktop computing, this generally translates as logging in with a standard user account and elevating to administrative privilege only as required. This is contrary to the common practice of using an administrator account on Microsoft Windows because traditionally many everyday tasks required root access to the operating system.
Removing administrative privilege considerably reduces the risk that users, or malicious processes running under a user’s account, might modify critical system settings or components that affect system stability, security or the integrity of the OS.
Microsoft Vista introduced User Account Control, an umbrella term for a set of technologies designed to make Windows easier to work with for standard users. UAC brings a number of changes that are useful in the enterprise, such as automation of file and registry writes from protected system folders to the user profile, making it less likely that legacy applications will fail to run under a standard user account.
Microsoft’s Application Compatibility Toolkit can be used to resolve some common problems encountered when running legacy applications as a standard user. Despite some help from UAC, moving to a least privilege model still poses technical challenges and should be fully tested before being implemented on production machines.
Implement Application Whitelisting
Many applications are now designed to run without needing to be installed. Sometimes referred to as “portable applications,” no special privileges are required to run these programs. The most well-known example is Google Chrome. While Chrome is a legitimate web browser, it’s not something you’d probably want users running without IT approval.
Before the advent of UAC, most viruses were built to run only on users who had admin privileges, and would fail to run otherwise. Standard user accounts are now more pervasive, so hackers are wising up to the fact that malware should be coded to run on a standard user to successfully compromise data.
Application whitelisting should be deployed to block malware, in turn helping to protect data that users access from the desktop. Software Restriction Policies can be configured in Windows XP and Vista to create a whitelist of pre-approved applications. SRPs weren’t readily adopted, and AppLocker in Windows 7 is designed to make implementing application control easier. Whitelisting is more practical than blacklisting, assuming you know what applications should be running on your systems.
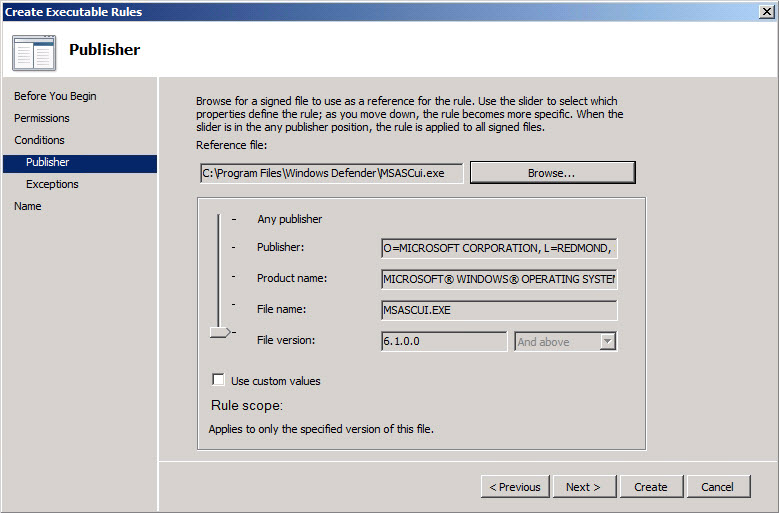
Figure 1 – AppLocker Publisher Rules in Windows 7
Update Third-Party Software
Patching Windows and other Microsoft software is important, but an increasing number of vulnerabilities exist in third-party applications, with Adobe Flash and Acrobat Reader being high on the list. Windows Update is no doubt handling your Microsoft patches, but you need to use additional software, such as System Center Configuration Manager, if you want to extend its functionality to include updating third-party software.
Group Policy Software Installation allows smaller companies to distribute patches using Windows Installer. But updating software using this method does require a lot of testing and may require repackaging software in Windows Installer format. Windows Intune 2 now supports third-party software installation.
Secure Your Network with Data Loss Prevention Tactics
While you could configure Windows Firewall to block outgoing traffic on nonstandard ports, the chances are that any malware infection looking for valuable data is going to call home using a protocol that it isn’t possible to block without crippling functionality. Monitoring outbound HTTP, HTTPS, FTP and SSL traffic is useful for helping to ensure that sensitive information doesn’t leak over any of these channels.
Web proxy servers, such as Microsoft’s Threat Management Gateway (TMG), can be deployed to filter common protocols. Microsoft’s solution includes optional client software that transparently redirects TCP and UDP traffic. Benefits include the ability to successfully proxy traffic for applications that require a secondary connection or have problems with authenticated proxies, authentication of TCP and UDP traffic, and a log of user names and applications that access remote servers.
While TMG does help control and monitor outbound traffic, it can’t detect sensitive data in outgoing communications; however, the URL filtering service can determine the malicious potential of destination sites. There are also host-based solutions that can be installed directly on desktops, such as McAfee’s Host Data Loss Prevention software.
Leverage IPsec Domain Isolation
Internet Protocol Security can be turned on in Windows to ensure network connections are established only between authenticated domain-joined devices. IPsec authentication is useful for protecting servers and clients from rogue devices, over which you have no control, that are connected to the LAN. IPsec can optionally be used for data encryption. Contrary to common belief, a certificate server isn’t required for IPsec domain isolation in a single Active Directory domain or forest. Starting in Windows Vista, the Windows Firewall with Advanced Security management console integrates IPsec with standard firewall rules, making it easier to deploy domain isolation.
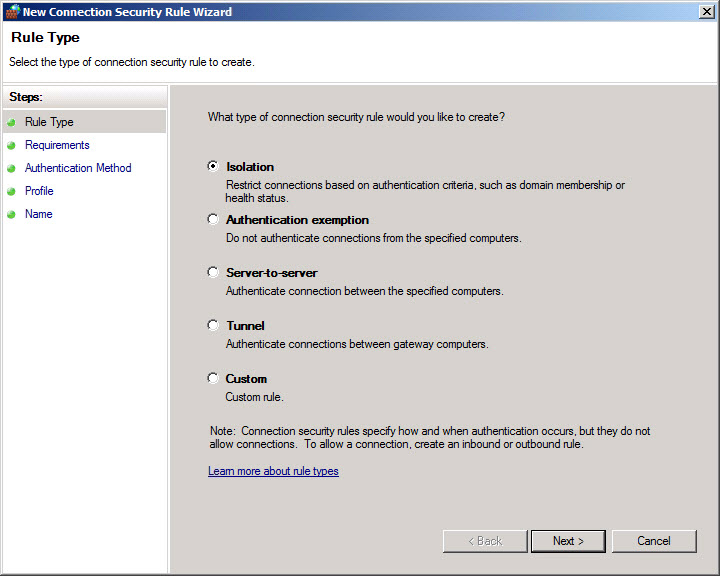
Figure 2 – Creating IPsec rules in the Windows Firewall with Advanced Security management console
Follow Best Practices
Third-party software updates, application whitelisting and maintaining standard user accounts are all crucial to secure desktop system security and should be implemented whenever possible. Data loss prevention and IPsec are optional, but they can significantly reduce risk depending on your environment.
These tips are not exhaustive but should provide a good starting point for organizations of all sizes looking to go beyond basic antivirus protection. Additionally, consider host-based DLP and security suites that include advanced malware protection.
For more information on DLP, visit CDW’s Data Loss Prevention Solution Center.








