A SIEM Solution That Plays Well with Others
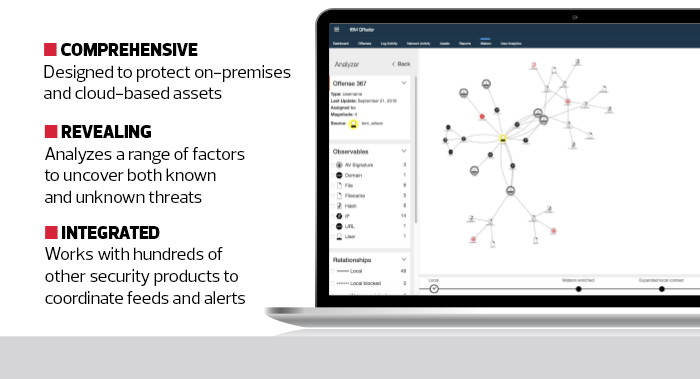
In cybersecurity, most companies pitch their products as the best and lobby their customers to remove everything else from their networks. IBM takes a different approach with QRadar and makes it easy to connect with almost any other kind of security device in order to coordinate defenses. Given that many college network defenses have grown up organically over time, this approach works well to protect campus networks.
To test this out, a QRadar instance was installed on a test network with a variety of other security appliances. Once configured, malware was introduced via a variety of paths, including one advanced persistent threat to test QRadar’s ability to coordinate defenses.
Setup of QRadar was surprisingly easy. Many of the security tools from other companies were automatically detected by QRadar and easily integrated into the appliance’s main interface. For those that were not detected, simply pointing the log files at QRadar was enough to trigger their inclusion.
For custom tools or log files generated by unique devices, QRadar provides an editor that makes onboarding those tools a quick process.
LEARN MORE: A proactive approach to avoiding zero-day attacks in higher education.
Once configured, we began to introduce malware to the test network using a variety of methods, from cloud-based incursions to direct introductions using endpoint hardware.
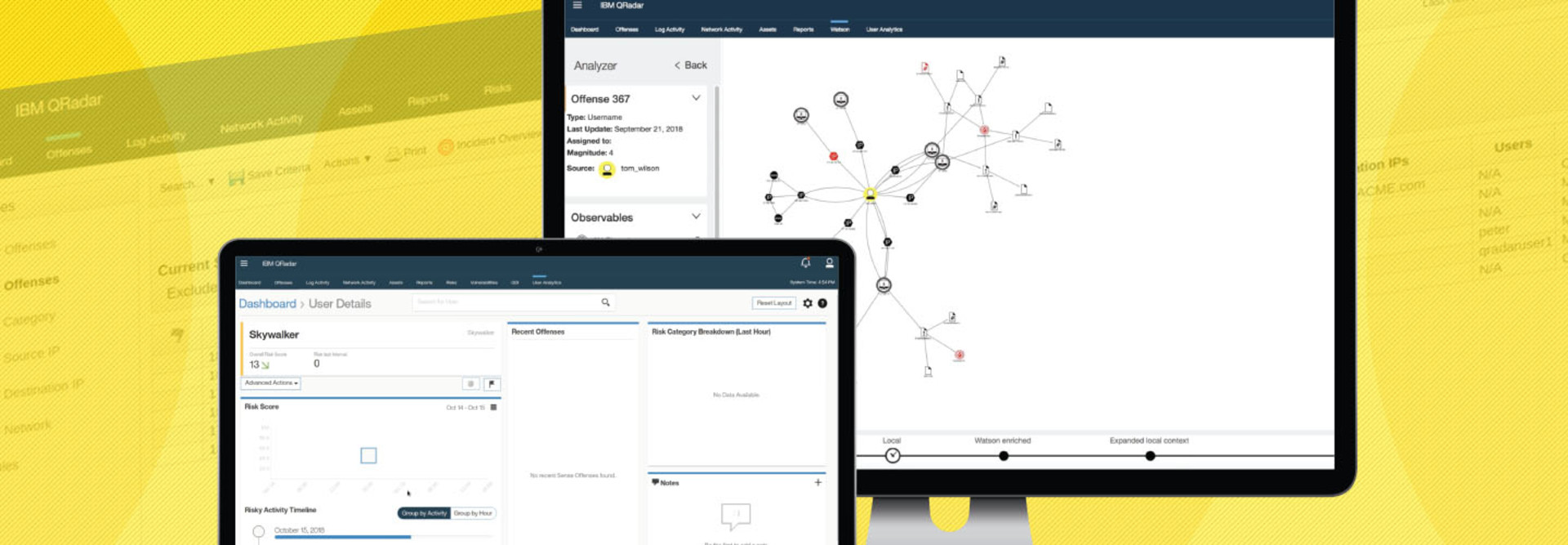
In all cases, the QRadar SIEM solution was able to detect those events and put them all in one place for analysis. It was even able to determine that several attacks were related, even though they were entering the test network from different avenues and were detected using different tools.
Despite the hodgepodge nature of the defenses, QRadar presented the situation in one place and helped to coordinate a unified defense. It also provided context for the attacks, correctly deducing that it was part of an ongoing campaign and showing how to prevent them from breaching defenses in the future.
As such, QRadar would be an invaluable tool and a real force multiplier for overworked IT staff trying to protect higher education networks. Its ease of use and simplicity of operations helps QRadar earn extra credit for its impressive performance.
SPECIFICATIONS
Device Type: Security Information and Event Management solution
Number of Supported Security Devices: 450+
Features: Threat detection, prioritization, investigation and response
Monitored Assets: Endpoints, network devices, cloud applications, threat intelligence, containerized assets, software services and others
Configuration: Hardware, software or virtual appliance