School IT Leaders Share Strategies on Defending Against DDoS Attacks
When the Florida Department of Education introduced computer-based standardized tests two years ago, the rollout wasn’t smooth. A distributed denial of service attack pummeled the testing vendor’s server, preventing students throughout the state from taking the test for three days.
As the testing vendor thwarted the attack and got the test back online, Miami-Dade County Public Schools faced repeated DDoS attacks of its own. The district’s IT staff saw a slowdown in internet speeds, realized what was happening and fended off the attacks by isolating and quarantining suspicious network traffic, allowing students to complete their tests.
“We successfully mitigated the attacks, and testing continued,” says Deborah Karcher, the district’s CIO. “But we’ve seen more attacks the past few years than we ever have, and they occur during the periods of time when we are testing."
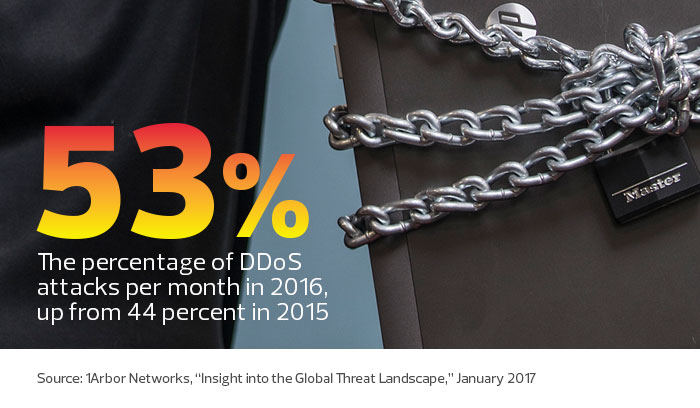
DDoS attacks, which overwhelm networks with massive amounts of traffic, are on the rise. For schools, the attacks can shut down websites, phone systems and prevent users from accessing the internet and applications.
More often than not, students are causing the cybermischief because they don’t want to take online tests or don’t want their parents to access their grades online, district IT leaders say.
“It’s so easy to launch attacks now,” says Mike Rothman, president of Securosis, a security research and advisory firm.
Schools face numerous types of DDoS attacks, Rothman says, including volumetric attacks, which try to flood inbound links, and application-oriented attacks, which take advantage of weaknesses in the operating system or the way an application is built. There are also protocol or state exhaustion attacks that target firewalls, load balancers and other infrastructure.
While school districts rely on their internet service providers (ISPs) to fight off large-scale DDoS attacks, district IT leaders use a combination of networking tools and network design to combat the attacks themselves.
Preventing Attacks Through Dropping Bad Traffic
The Utah Education Network (UEN), which provides high-speed internet access to the state’s school districts, universities and state government agencies, recently invested in enterprise-class DDoS mitigation technology.
The statewide network considered several solutions, but it ultimately chose on-premises equipment that it installed on its own private cloud.
The technology, installed 18 months ago, automatically detects and blocks DDoS attacks by using a feature called Unicast Reverse-Path Forwarding to silently drop — or “blackhole” — the bad traffic, says Troy Jessup, UEN’s associate director of network and security operations.
The mitigation system can also scrub traffic. As traffic enters the network backbone, scrubbers allow legitimate traffic to pass through, while blocking malicious traffic.
“It’s very effective, and smart enough to make those decisions,” Jessup says. Utah school districts are targeted by DDoS attacks several times a week. UEN previously mitigated attacks manually by using NetFlow technology to analyze traffic patterns, and if an in-house system detected anomalies, the staff manually blackholed the bad traffic.
UEN’s new mitigation system has been configured to automatically stop an obvious DDoS attack. But if it’s questionable, the system will notify the IT staff to investigate further.
“We err on the side of caution,” Jessup says. “If it’s something that could be an attack or legitimate traffic, we get alerted, and then we take a look at it.”

Enhanced Network Monitoring During Critical Periods
In Florida, Miami-Dade County Public Schools primarily gets hit by DDoS attacks during testing, Karcher says.
“We are on a heightened level of awareness during testing,” she says. “We watch our network, and it allows us to react a lot more quickly.”
The IT staff mitigates the risk by using network monitoring tools and creating rules on its networking equipment (routers, switches, firewalls and intrusion prevention systems) to automatically spurn those attacks, says Paul Smith, director of data security and technical services.
“These attacks are not obvious, but we’ve tuned our tools to pick up the right metrics,” he says. “Sometimes we get a call from our ISP telling us we’re under attack, and we find out that we’ve already mitigated it with the tech we have in place.”
Critical Countermeasures Stop Attacks
In Illinois, the St. Charles Community Unit School District 303 is taking advantage of built-in intrusion detection and prevention in its firewall and the Border Gateway Protocol (BGP) to stop DDoS attacks.
In some cases, the IDP tool automatically stops DDoS attacks. In others, it alerts district network analyst Jeff McCune that an attack is happening so he can manually defend against it.
BGP allows him to blackhole IP addresses that are being attacked. If an IP address at a high school is under attack, for example, he uses his network’s management tool to manually drop those bad packets. Then he uses the tool to alert the broader community, including his two ISPs, so they can drop the packets before they reach the school network.
“I can put it into a BGP community so that any router that does BGP won’t pass the traffic,” he explains.
McCune has also increased the number of IP addresses the district uses from five to 254 to remap the entire internal network. He uses different IP addresses for the district’s headquarters and each of its 17 schools so he can pinpoint which address is being attacked.
He took these steps after two high school sophomores launched a series of attacks, ranging from 30 minutes to four hours, over a six-week period in 2014.
After installing countermeasures, McCune used BGP to fend off a DDoS attack aimed at a middle school’s wireless network. “I was able to shut it down within 15 minutes because I could see where it was coming from,” he says.
Network Design for Optimal Damage Control
Using the right network architecture can minimize damage from a DDoS attack, says Jeremy Cox, network manager and information security officer at Washington County School District in Saint George, Utah.
When districts have only one firewall installed, a DDoS attack can disrupt access to the internet and to internal applications. And if districts rely on Session Initiation Protocol trunks for a Voice over IP phone system, it will also bring down phone services, Cox says.
To protect against this, Washington County School District has a main firewall at the border and internal firewalls to protect the internal network. In addition, for its VoIP system, the district uses a Primary Rate Interface connection that terminates inside the firewall.
That way, if a DDoS attack manages to stop internet access temporarily, phone service will still work, and district employees will be able to access important business applications, Cox says.
“Network design is the real key,” he says.








